Lightsail
Continue reading “Amazon Lightsail”
Amazon Elastic Compute Cloud (EC2)
AMI Virtualization Types Continue reading “Amazon Elastic Compute Cloud (EC2)”
Protecting Network Boundaries
VPC (Virtual Private Cloud)
- Isolate workloads into separate VPCs (based on application, department, test, dev, etc.)
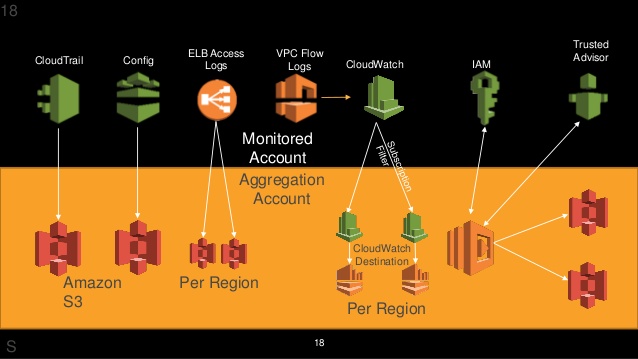
Monitoring to enhance security
AWS CloudTrail
- Provides a log of all request for AWS resources in your account.
- You can see what service was accessed, what action was performed and who made the request.
- Captures information about every API call to every AWS resource, including sign-in events.
- After you have enabled AWS ClodTrail event logs are delivered every five minutes.
- Stores log in S3.
- For additional security, when creating a trail, enable SSE-KMS encryption and log file validation.
- It can take up to 15 minutes between the time an event occurs and when the CloudTrail creates the log file containing the event.
Securing AWS Cloud Services
Key Pairs
Amazon EC2 instances created from a public AMI use a public/private key pair instead of a password for signing in via SSH. The public key is embedded in your instance, and you use the private key to sign in securely without a password. After you create your own AMIs, you can choose other mechanizms to log securely to your new instances.