Key Pairs
Amazon EC2 instances created from a public AMI use a public/private key pair instead of a password for signing in via SSH. The public key is embedded in your instance, and you use the private key to sign in securely without a password. After you create your own AMIs, you can choose other mechanizms to log securely to your new instances.
Amazon CloudFront key pair can be created only by the root account and cannot be created by IAM users.
X.509 Certificates
X.509 Certificates are used to sign SOAP-based requests. They contain a public key and additional metadata (for example an expiration date that AWS verifies when you upload the certificate) and is associated with a private key.
KMS – Key Management Service
AW Key Management Service (KMS) provides regional, secure key management and encryption and decryption services. KMS is FIPS 140-2 level 2 validated, and certain aspects support level 3 (exam hint). Everything in KMS is regional. KMS can use CloudHSM via Custom Key Stores (FIPS 140-2 Level 3)
KMS manages customer master keys (CMK), which are created in a region and never leave the region or KMS. They can encrypt or decrypt data up to 4 KB. CMKs have key policies and can be used to create other keys.

- KMS can encrypt data up to 4 KB with a CMK — you supply the data and specify the key to use.
- It can decrypt data up to 4 KB — you provide the ciphertext, and it returns the plaintext.
- You can also re-encrypt up to 4 KB — you supply the ciphertext, the new key to use, and you are returned new ciphertext (at no point do you see the plaintext).
KMS can generate a data encryption key (DEK) using a CMK. You or a service can use a DEK to encrypt or decrypt data of any size. KMS supplies a plaintext version and an encrypted version.
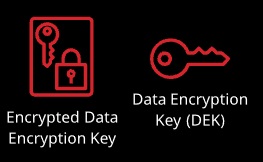
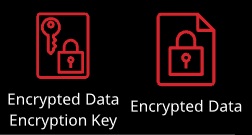
The encrypted DEK and encrypted data can be stored together. KMS is used to decrypt the DEK, which can then decrypt the data.
- Provides a simple interface used to generate and manage cryptographic keys
- Operate as a cryptographic service provider for protecting data.
- Easy way to control access to your data using managed encryption
- Integrated with AWS services including EBS, S3, and RedShift to simplify encryption of your data
- Create, rotate, disable, enable, and define usage policies for master keys
- KMS keys are region-specific
- Data encrypted under a key becomes irretrievable if the key is lost
- Key usage is recorded in CloudTrail logs for audit purposes
CloudHSM (Hardware Security Module)
- Dedicated hardware security modules under your exclusive control
- Designed to store and process cryptographic keys securely
- FIPS 140-2 Level 3 compliance
- Designed to integrate with VPC
- Integrates with PKCS#11, Java JCE, and Microsoft CNG
- Can connect to CloudHSM from your on-premises datacenter using VPN or AWS Direct Connect
AWS Certificate Manager (ACM)
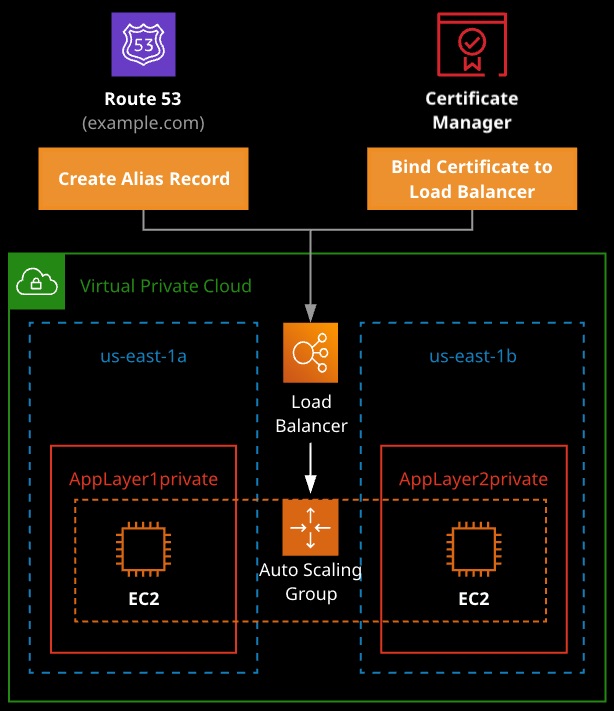
- Service that lets you provison, manage and deploy SSL/TLS certyficates for use with AWS cloud services.
- Native integration with ELB, CloudFront, Elastic Beanstalk, and API Gateway
- No cost associated with certificates — only the resources with which they are used
- Certificates automatically renew when actively used with supported services
- Integrates with Route 53 to perform DNS checks as part of the certificate-issuing process
- ACM is regional — certificates can be applied to services in that region only