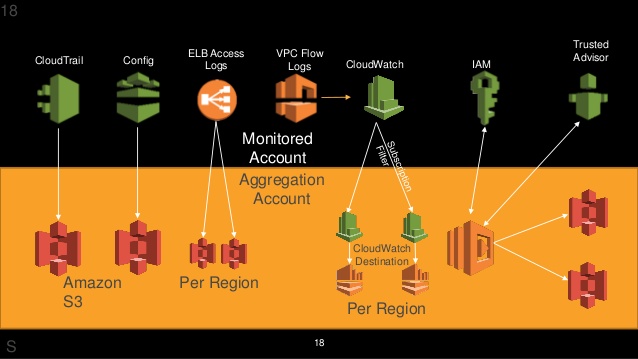
AWS CloudTrail
- Provides a log of all request for AWS resources in your account.
- You can see what service was accessed, what action was performed and who made the request.
- Captures information about every API call to every AWS resource, including sign-in events.
- After you have enabled AWS ClodTrail event logs are delivered every five minutes.
- Stores log in S3.
- For additional security, when creating a trail, enable SSE-KMS encryption and log file validation.
- It can take up to 15 minutes between the time an event occurs and when the CloudTrail creates the log file containing the event.
Amazon Cloudwatch
- Can monitor the use of AWS resources.
- There are standard metrics ans users can create their own custom metrics.
- CloudWatch Logs can agregate logs from multiple sources for easy storage and searching including:
– CloudTrail Logs
– VPC Flow Logs
– RDS Logs
– Route 53 DNS Queries
– Lambda
Amazon Athena
- AWS uses S3 to store logs. Athena let you use SQL to search data stored in S3.
- Although you can use CloudWatch Logs to store and search logs, only Athena give you the ability to format the output.
- You can import multiple logs into a single Athena database. Athena supports data formats: CSV, JSON, Apache ORC and Parquet (format for Apache Hadoop).
Amazon VPC Flow Logs
- Can capture information about the IP traffic going to and from network interfaces in your Amazon VPC.
- Flow log data is stored using CloudWatch Logs.
- After you have created a flow log, you can view and retrieve its data in Amazon Cloud Watch Logs.
In addition Elastic Load Balancing and elastic network interfaces provide access logs that capture detailed information about requests or connections sent to your load balancer. Each log contains information such as time it was received, the client’s IP address, latencies, requests paths, and server responses.
Amazon GuardDuty
- Analyzes VPC flow logs, CloudTrail management event logs, and Route 53 DNS query logs, looking for known malcious IP address, domain names, and potentially malcious activity.
- When GuardDuty detects a potential security problem, it creates a finding, which is a noticication that details the questionable activity.
- GuardDuty displays the finding in GuardDuty console and also delivers the finding to CloudWatch Events.
- You can configure SNS notification to send an alert or take an action in response to such an event.
- Finding types: Backdoor, Behavior, Cryptocurrency, Pentest, Persistance, Recon, ResourceConsumption, Stealth, Trojan, UnauthorizedAccess.
AWS Config
- Record configuration changes to an AWS account.
- Can be used to identify new and deleted resources.
- Can issue notification when resource configuration change.
AWS Config Rules
- Allow set up the rules to check confguration changes recorded by AWS Config.
- There are prebuilt rules provided by AWS.
- You can create your own rules, which will run on AWS Lambda.
- Rules are invoked automatically when triggered to provide continuous assessment.
- AWS Config can trigger a rules evaluation when any resourcee that matches the rule’s scope changes in configuration.
- A rule can also be triggered to evaluate your account’s configuration periodically.
AWS config use cases include the following:
- Resource discovery
- Troubleshooting
- Change management
- Audit compliance
- Security analysis
Amazon Inspector
Automated security assesment service that helps improve the security and compliance of application deployed on AWS.
Inspector can:
- Analyze the behavior of your AWS resources
- Test network accessibility and security state
- Assesses for security vulnerabilities and deviations from best practices
Target: A collection of EC2 instances
Assessment Template: Composed of security rules and produces a list of findings
Assessment Run: Applying the assessment template to a target
Findings: Security report, organized by severity level
Features:
- Configuration scanning and activity monitoring engine
– Determines what a target looks like, its behavior, and any dependencies it may have
– Identifies security and compliance issues
- Built-in content library
– Rules and reports built into Inspector
– Best practice, common compliance standard, and vulnerability evaluations
– Detailed recommendations for resolving issues
- API automation
– Allows for security testing to be included in the development and design stages
NOTE: AWS does not guarantee that following the provided recommendations will resolve every potential security issue.

AWS Trusted Advisor
Provides real-time guidance to help ensure adherence to AWS best practices.
- Allows an AWS customer to get reports on their environment, including:
• Cost Optimization,
• Performance Security,
• Fault Tolerance,
• Service Limits
- Available to all customers:
– Access to seven core checks:
• S3 Bucket Permissions
• Security Groups – Specific Ports Unrestricted
• IAM Use
• MFA on Root Account
• EBS Public Snapshots
• RDS Public Snapshots
• Service Limits
- Available to Business and Enterprise Support customers
• Access to the full set of checks
• Notifications
• Weekly updates
• Create alerts and automate actions with CloudWatch
• Programmatic access
• Retrieve results from the AWS Support API