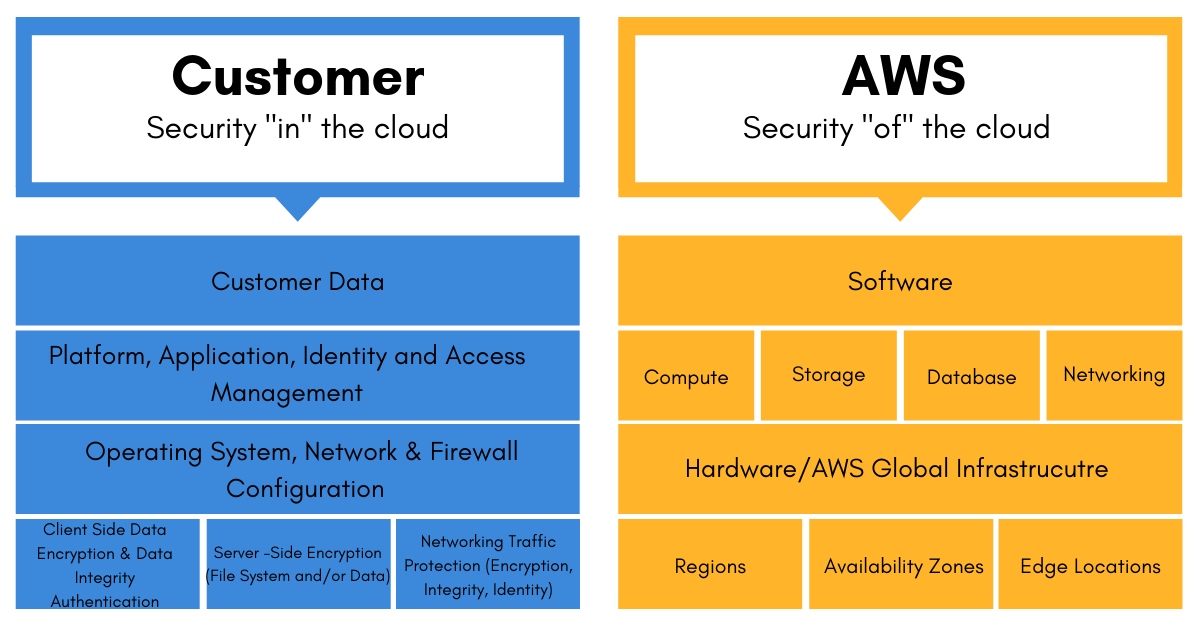
Customer
Responsible for security IN the cloud
• Customer Data
• Platform, Application, and IAM
• OS Patching on EC2
• Antivirus
• Network, and Firewall Configuration
• Multi-Factor Authentication
• Password and Key Rotation
• Security Groups
• Resource-Based Policies
• Access Control Lists
• VPC
• Operating-system-level patches
• Data in transit and at rest
AWS
Responsible for security OF the cloud
• Regions, Availability Zones, and Edge Locations
• Physical server level and below
• Fire/power/climate management
• Storage device decommissioning according to industry standards
• Personnel Security
• Network Device Security and ACLs
• API access endpoints use SSL for secure communication
• DDoS protection
• EC2 instances and spoofing protection (ingress/egress filtering)
• Port scanning against rules even if it’s your own environment
• EC2 instance hypervisor isolation Instances on the same physical device are separated at the hypervisor level; they are independent of each other Underlying OS patching on Lambda, RDS, DynamoDB, and other managed services; customer focuses on security