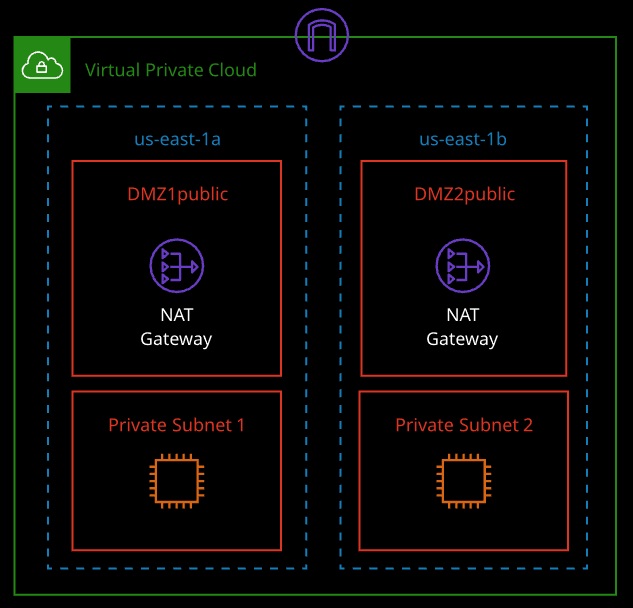
VPC (Virtual Private Cloud)
- Isolate workloads into separate VPCs (based on application, department, test, dev, etc.)
Security features in Amazon VPC include:
- Network ACLs
- Security groups
- Routing tables
- External gateways
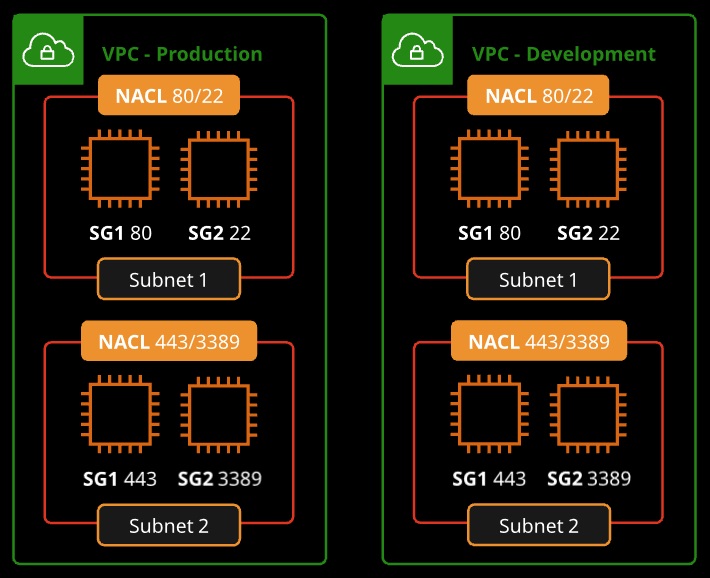
NACLs (Network Access Control Lists)
- Works at the subnet level
- Stateless = inbound and outbound rules are separate, no dependencies
- Granular control over IP protocols (allow and deny rules for inbound and outbound evaluated in order)
- Work with security groups (NACL applies for the whole subnet, security groups apply to members)
- Ephemeral ports: Client requests depending on OS (ports 1024-65535)
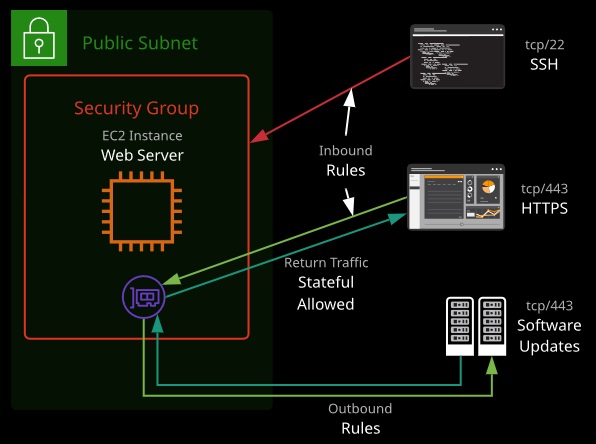
Security Groups
Security groups are software firewalls that can be attached to network interfaces and (by association) products in AWS. Security groups each have inbound rules and outbound rules. A rule allows traffic to or from a source (IP, network, named AWS entity) and protocol.
Security groups have a hidden implicit/default deny rule but cannot explicitly deny traffic.
They are stateful — meaning for any traffic allowed in/out, the return traffic is automatically allowed. Security groups can reference AWS resources, other security groups, and even themselves.
- Works at the interface level
- Default group enables inbound communication from other members of the same group and outbound communication to any destiny.
- Group instances with similar functions
- Stateful = every allowed TCP or UDP port will be allowed in both directions
Host-Based Firewalls: OS-level firewalls as needed
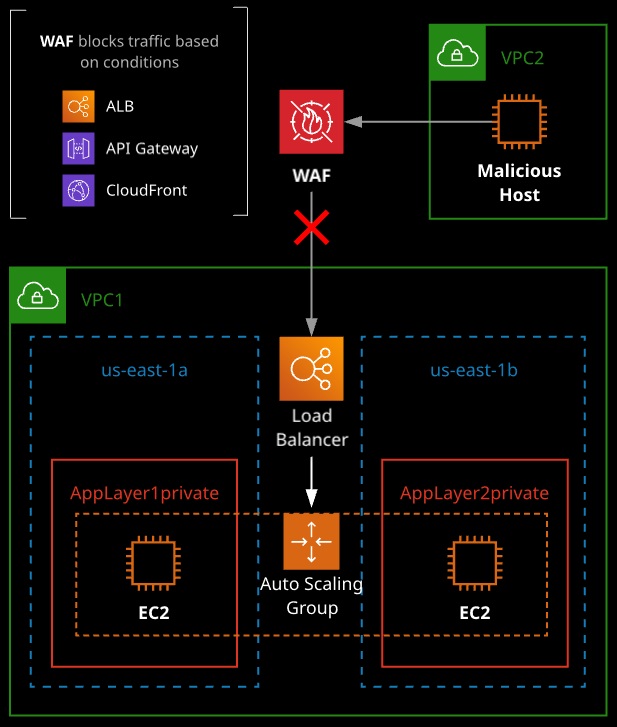
AWS Web Aplication Firewall (AWS WAF)
- WAF rules are based on conditions, such as:
• IP addresses
• HTTP headers
• HTTP body
• Uniform Resource Identifier (URI) strings
• SQL injection
• Cross-site scripting (XSS)
- Integrated with AWS services:
• CloudFront
• API Gateway
• Application Load Balancer
- When using WAF on ALB, rules run in region
AWS Shield
- Service that helps protect your applications from DDoS attack.
- Mittigates 99% of attacks in 5 minutes or less.
- Mittigates attacks aganist Elastic Load Balancing in less than 5 minutes.
- Mittigates attacks aganist CloudFront and Route 53 in less than 1 second
- Usually mitigates all other attack in less than 20 minutes.
Two flavors of AWS Shield:
- Standard – defends aganist common layer 3 and 4 DDos attacks as SYN flood and UDP reflection attacks. Shield standard is automatically activated and no additional cost for all AWS customers.
- Advanced – provides the same protection as Shield Standard but also includes protection aganist layer 7 attacks, such as HTTP flood attacks that overhelm an application with HTTP GET or POST requests. EC2 instance must have elastic IP address to obtain layer 7 protection. You also get attack notifications, forensic reports, and 24/7 assistance from AWS DDoS response team. AWS WAF is included at no charge.
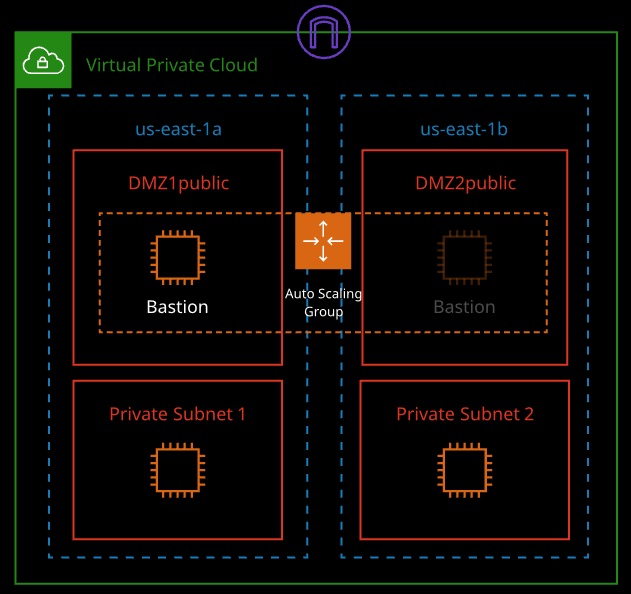
Bastion Hosts
- “Gate” that protects our infrastructure but allows access for updates or other management
- Used to control remote access (e.g., via RDP or SSH)
- These should be hardened and secured very carefully and regularly
- Can have an Elastic IP address that never changes and can be whitelisted
- We can have standby bastion hosts for higher availability
NAT Gateways
- Enable instances in a private subnet to access the Internet for updates
- The instances in a private subnet are not accessible via the Internet
- If updates/outside communication is business critical, consider using multiple NAT gateways