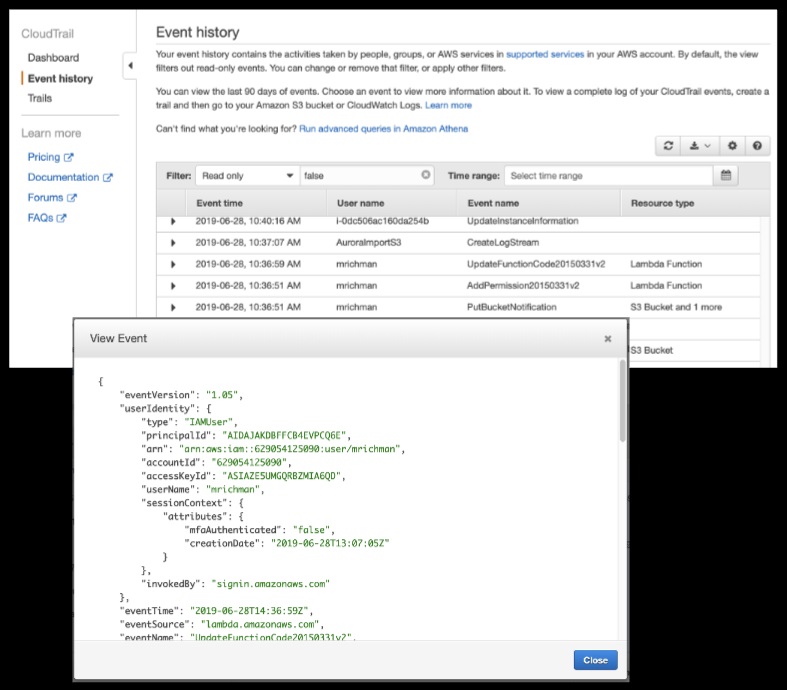
CloudTrail is a governance, compliance, risk management, and auditing service that records account activity within an AWS account. Any actions taken by users, roles, or AWS services are recorded to the service. Activity is recorded as a CloudTrail event, and by default you can view 90 days via event history.
Trails can be created, giving more control over logging and allowing events to be stored in S3 and CloudWatch Logs.
Events can be management events that log control plane events (e.g., user login, configuring security, and adjusting security groups) or data events (e.g., object-level events in S3 or function-level events in Lambda).
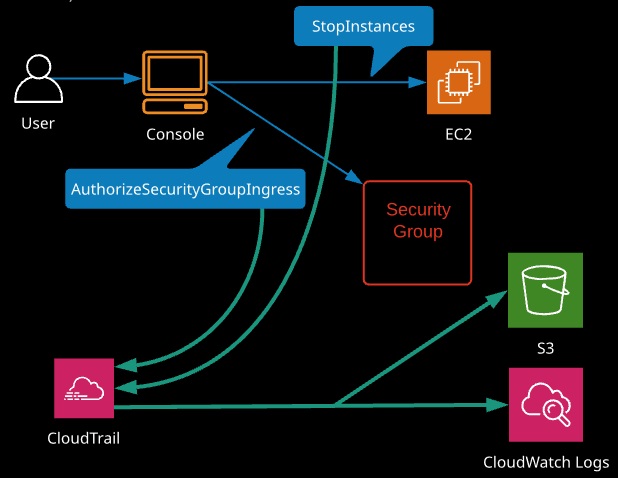
- Allows for auditing of your AWS environment
- Logs every API call to your resources (Console, AWS CLI, SDK)
- Every interaction with AWS is an API call
- Can provide information for many types of activities:
- Governance
- Compliance
- Operational auditing
- Risk auditing
- Trail: Configuration allowing for event logging from all regions to a single S3 bucket:
- Can be analyzed by your preferred tool from there
- Can also report to CloudWatch Logs for near real-time monitoring and alerting