We have such a yaml template:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 |
Parameters: VPCId: Description: VPC to create the security group into Type: AWS::EC2::VPC::Id CidrSSH: Type: String Default: "0.0.0.0/0" CidrHTTP: Type: String Default: "0.0.0.0/0" Resources: SSHSecurityGroup: Type: "AWS::EC2::SecurityGroup" Properties: GroupDescription: Test Drift SSH Security Group SecurityGroupIngress: - CidrIp: !Ref CidrSSH FromPort: 22 ToPort: 22 IpProtocol: tcp VpcId: !Ref VPCId CriticalSecurityGroup: Type: "AWS::EC2::SecurityGroup" Properties: GroupDescription: Test Drift HTTP Security Group SecurityGroupIngress: - CidrIp: !Ref CidrHTTP FromPort: 80 ToPort: 80 IpProtocol: tcp VpcId: !Ref VPCId |
And a json Stack Policy:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 |
{ "Statement": [ { "Effect": "Allow", "Action": "Update:*", "Principal": "*", "Resource": "*" }, { "Effect": "Deny", "Action": "Update:*", "Principal": "*", "Resource": "LogicalResourceId/CriticalSecurityGroup" }, { "Effect" : "Deny", "Action" : "Update:*", "Principal": "*", "Resource" : "*", "Condition" : { "StringEquals" : { "ResourceType" : ["AWS::RDS::DBInstance"] } } } ] } |
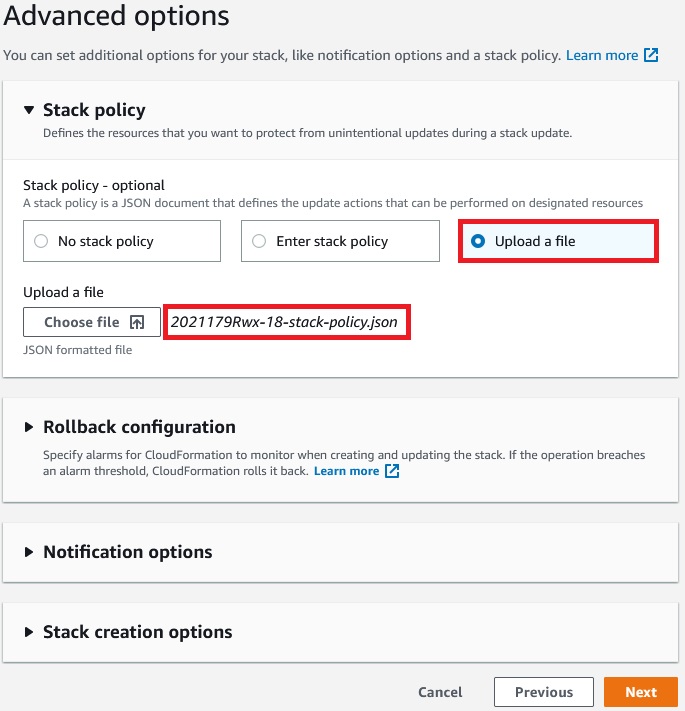
This stack policy which will allow us to update SSHSecurityGroup but update of CriticalSecurityGroup will be denied.
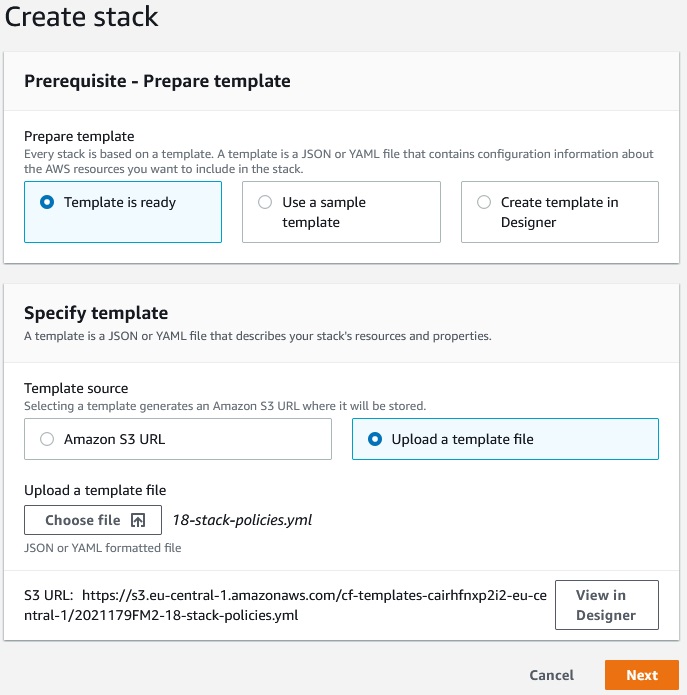
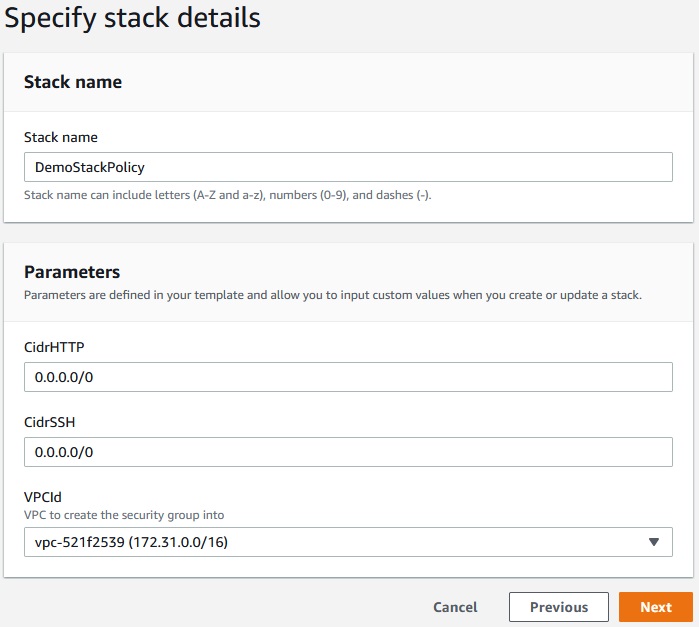
So lets’s create a stack:
Next ->
Next ->
Next -> Create stack
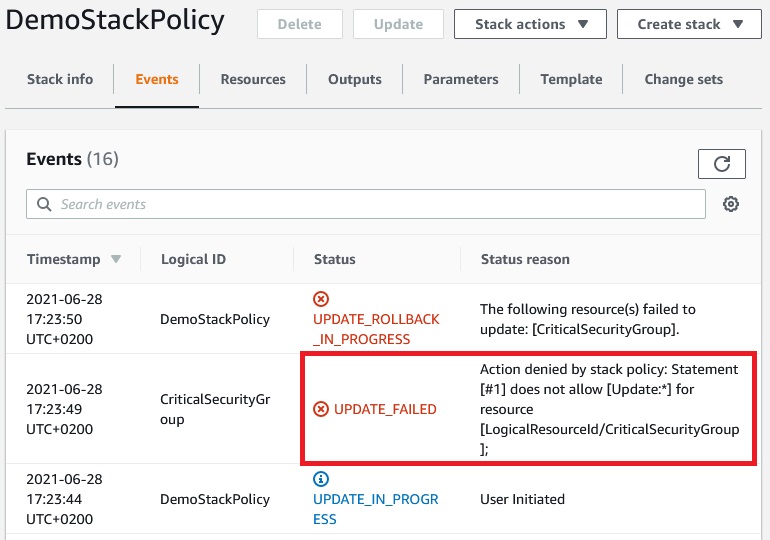
The Stack has been created with stack policy. Now let’s try to update it.
First we will update CidrSSH subnet:
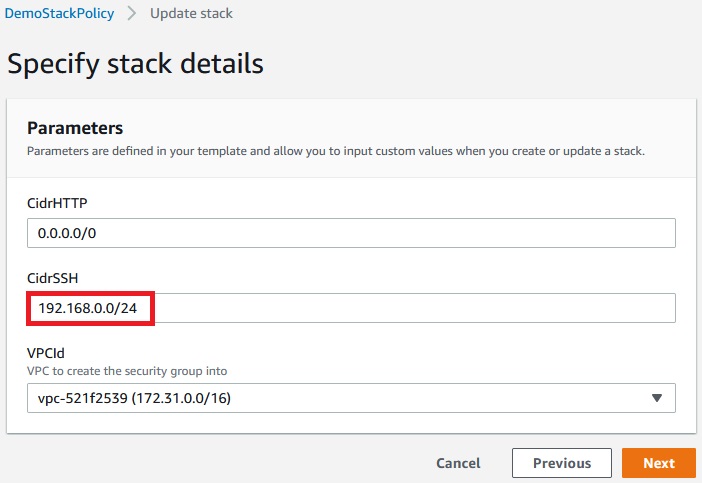
Next -> Next -> Update stack
And update has finished because stack policy allowed for this.
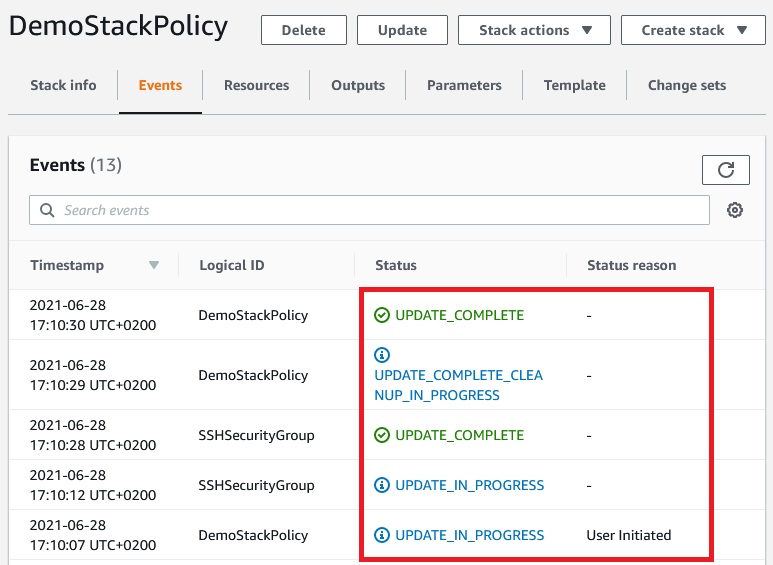
Now let’s try to update CidrHTTP:
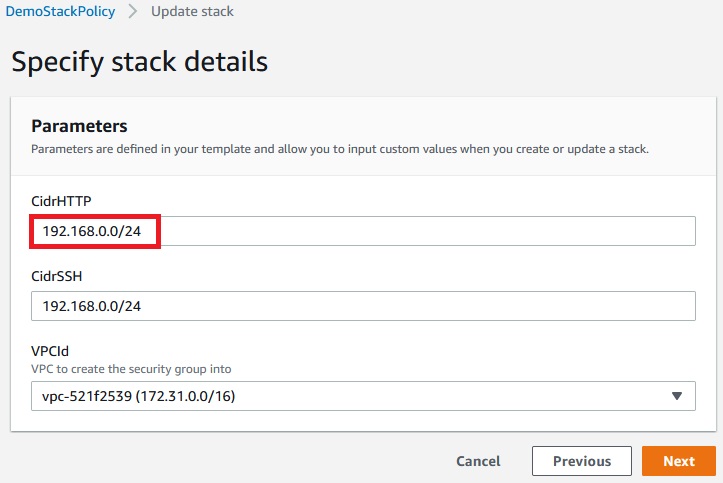
Next -> Next -> Update stack
Update of stack has failed because action was denied by the stack policy.